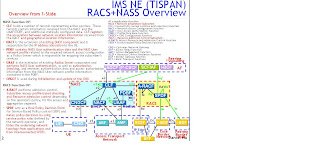
+(1-Slide).jpg)
NASS = Network Attachment Subsystem
CLF = Connectivity session Location and repository Function
NACF = Network Access Configuration Function
UAAF = User Access Authorization Function
PDBF = Profile Data Base Function
CNGCF = CNG Configuration Function
RACS = Resource Admission Control Subsystem
A-RACF= Access-Resource and Admission Control Function
SPDF = Service-based Policy Decision Function
AF = Application Function
CNG = Customer Network Gateway
ARF = Access Relay Function
AMF = Access Management Function
RCEF = Resource Control Emulation Function
BGF = Border Gateway Function
BTF = Basic Transport Functions
NASS Function OV:
- CLF holds a number of records representing active sessions. These records contain information received from the NACF and the UAAF/PDBF, and additional statically configured data. CLF registers the association between network location information received from the NACF and geographical location information.
- NACF is the extension of existing DHCP component and is responsible for the IP address allocation to the UE.
- PDBF contains NASS User authentication data and the NASS User network profile related to the required network access configuration as a Policy Server which is responsible for mapping the subscriber’s services
- UAAF is the extension of existing Radius Server component and performs NASS User authentication, as well as authorization checking, and retrieves authentication data and access authorization information from the NASS User network profile information contained in the PDBF.
- CNGCF is used during initialization and update of the CNG
RACS Function OV:
- A-RACF performs admission control, Subscriber access profile-based checking and Resource admission control depending on the operator's policy, for the access and aggregation segment.
- SPDF acts as a final Policy Decision Point for Service-Based Policy control (SBP) and makes policy decisions by using service policy rules defined by the network operator, and hides the underlying network topology from applications and from interconnected SPDFs.
Further Information: https://docs.google.com/fileview?id=F.6000c46a-184d-406c-a1d0-1ffa4bf8d82b&hl=en
沒有留言:
張貼留言